An all-in-one workspace, Notion lets users write, plan, collaborate, and organize all their tasks and notes in one space. Notion's main selling point is an uncluttered design and lightweight editor that lets users focus on getting work done without interruptions.
Although Notion's minimalist design is certainly a main attraction for returning users, Notion smartly recognized that too much white space could actually be unnerving for new users, who don't yet know how to access the product's numerous features and functionalities.
Set and complete your most important priorities with this template. The Eisenhower Matrix is a four. Notion offers three unique functions over the rivals – Blocks, Commands, and Templates. The whole software is designed to move blocks around the pages which makes pages-based projects easier to.
So Notion guides new users through a brief, hands-on onboarding process that introduces the product's key features, functionalities, and commands—ensuring that users have the skills and resources they need to start using the tool straight away.
A comprehensive library of templates also introduces users to Notion's diverse range of use cases—helping new users immediately understand the product's potential value.
But before we get into all that, let's take a quick look at Notion's signup process, which is delightfully pared back and visually pleasing, thanks to minimal design and a friendly mascot.
Creating an account
Signing up for a new account is easy, and there is an option to signup using your Google or Facebook accounts—a small timesaver that nonetheless feels like a big convenience for the user.
Notion does a great job with their UX copy. It's succinct, colloquial, and reassuring—and optional fields are clearly labeled. A simple progress indicator lets people know where they're at in the account creation process, and CTA lets users know what the next steps will accomplish.
The third and fourth steps in the process are optional. First, users are asked if they would like to import data from their existing tools. This is helpful for high-intent signups who want to dive into their own material straight away, but Notion is smart to keep this step optional, since connecting to an existing techstack is a big ask for folks who may be evaluating Notion more casually.
Finally, Notion includes a bit of cross-selling for their mobile, desktop, and web clipper apps. Again, this step is optional.
Learn-by-doing onboarding
With that, users are free to explore the app. But instead of dropping new users into a complex dashboard, Notion introduces them to the core features with a lightweight interactive tutorial.
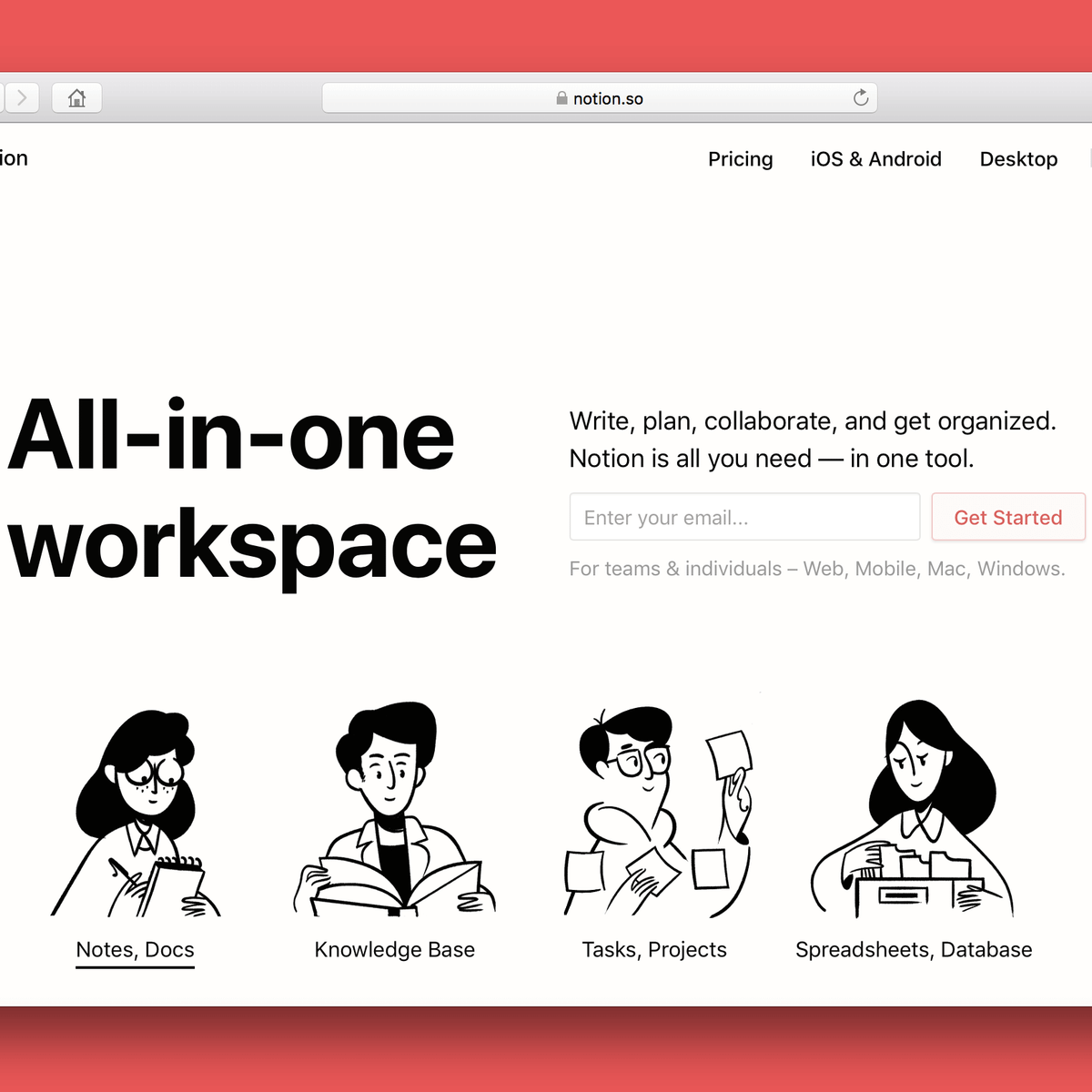
Notion's Getting Started page is a great example of learn-by-doing onboarding. Notion teaches new users the actions they'll need to access their product's core value (and then some) with a fully functional checklist, that includes simple instructions like 'Type '/' for slash commands.' High-contrast tooltips appear when users hover over certain page elements to provide further instruction as they explore the interface on their own.
Notion Example Sentence
Inspirational templates
Example Of Notion
Notion also offers a comprehensive library of templates—very helpful for a product with so many possible use cases. Instead of overwhelming users with the full list of templates, Notion uses the information provided by the user during signup to offer a personalized selection of 5 templates that the individual user is likely to find most helpful. Since we said we were in marketing, we've been given a shortlist of marketing-related templates to browse through.
Clicking on any template in the side menu triggers a large modal with a preview of the selected template. Like the Getting Started doc, each template uses the interface itself to instruct users, and demo data helps visualize value.
From this window, users can explore the full list of templates for work and personal use. For example, we discovered an intriguing use case for travel planning that immediately added another layer of value to an already amazing product.
Why this is really good UX:
- Notion maintains a clean, minimalist design throughout. This visually reinforces their promise to potential users: an uncluttered writing and organization space that won't distract you with unnecessary bells and whistles.
- The signup flow not only helps Notion to personalize the workspace according to each user's specific needs (depending on the function they'll use it for and whether they'll use individually or as a team), but it also helps reassert that Notion is a powerful, multifunctional, multichannel solution that can take the place of many existing tools across multiple platforms.
- The Getting Started page is a great example of learn-by-doing onboarding that lets new users learn how to use the product... by using the product. Clear instructions make it easy to explore and get the hang of 'hidden' features and functionalities that would not be obvious to first-time users otherwise.
- Templates are a great way to not only add value, but convey it clearly. The curated list of templates that Notion provides to each user help them dive into more advanced use cases quickly, while the full list of templates also serves the purpose of showcasing additional use cases that are possible with this visually lightweight but functionally robust product.
Watch the video
Editor's note: The video above—starring our friend Tristan Harward, former Head of Product Design at Appcues—was filmed in 2018 and refers to an older (but very similar) version of Notion's onboarding UX. The important takeaways remain the same.
The internet is huge, but even in this vast global network, there's a lack of space. The system of IP addresses as we are currently using it (IPv4), has been long exhausted. All possible addresses (at least 4,294,967,296) have already been assigned. A solution had to be thought up a few decades ago to solve the problem. CIDR helps extend the amount of available addresses.
What was intended as a temporary solution has now been active for over 20 years. And since the widespread introduction of IPv6 is still a long time coming, CIDR will probably still be around for years to come. This is reason enough to learn more about class inter-domain routing.
- Calculating CIDR: examples
Why was CIDR developed?
As early on as 1993, it was clear that the internet was growing quicker than had initially been anticipated. So, a solution was needed, which meant abandoning the network classes. The IP addresses were originally divided into five classes. If a company wanted to be connected to the internet, it had to choose an IP address from the appropriate class. For each class, different numbers of octets (the four numerical blocks of IP addresses) were used to identify the networks. The remaining octets determined the number of hosts in a network.
| Class A | Class B | Class C | Class D | Class E |
|---|---|---|---|---|
| 0.0.0.0 - 127.255.255.255 | 128.0.0.0 - 191.255.255.255 | 192.0.0.0 - 223.255.255.255 | 224.0.0.0 - 239.255.255.255 | 240.0.0.0 - 255.255.255.255 |
For example, a class A network could accommodate over 16 million hosts, but only 128 (0-127) of these networks were available. In class B, on the other hand, slightly more than 16,000 networks were possible, but each network could contain 65,534 hosts. The networks in class C only had an octet left and could only accommodate 254 (1-254, since 0 and 255 are always reserved) hosts.
This shows that the classification just wasn't practical in most cases. For many companies, a network with only 254 participants was far too small, but several thousands of hosts need the fewest networks. This ultimately led to a lot of waste, since companies inevitably had to collect unused addresses. To meet the needs of internet users better, it was decided to make the network sizes more flexible, to reduce the size of routing tables in internet routers, and to slow down the decrease in the number of available IP addresses.
Routing tables are located in a router and help find the way to the correct destination address. Data packets pass through many nodes from origin to destination. For routers to recognize what the optimal path through the network looks like, a corresponding table is fed with information. The size of the file grows exponentially when a path has to be introduced for every possible target. Since CIDR assembles addresses into blocks, it is no longer necessary to store so much information in the routing tables. This means that several addresses are combined into one route.
How does CIDR work?
CIDR is based on the idea of subnet masks. A mask is placed over an IP address and creates a sub network: a network that is subordinate to the internet. The subnet mask signals to the router which part of the IP address is assigned to the hosts (the individual participants of the network) and which determines the network.
Instead of adding a subnet mask, a specification in the form of suffixes can also be integrated directly into the IP address using classless inter-domain routing. But this not only shortens the display: CIDR also makes it possible to create supernets in addition to subnets. This means that it is not only possible to subdivide a network more precisely, but also to combine several networks.
Supernets are important, for example, if a company has several locations but wants to deal with all computers in the same network. Supernets allow several networks to be combined into one route, which is why this technology is also called route aggregation (i.e. grouping of routes). This means that data packets are only sent to one destination – regardless of where the hosts are located.
VLSM is an important part of CIDR: the variable length subnet mask allows subnets to be realized with variable lengths and not only in size order of the network classes.
The CIDR notation
An IP address made it possible in the past to determine which class it belonged to. For example, the class C networks were located between the addresses 192.0.0.0 and 223.255.255.255. A subnet mask (e.g. 255.255.255.0) is like a mask on top of the IP address and specifies the hosts. In CIDR format, this information is stored as a suffix in the IP address itself. However, the basic principle remains the same: the suffix specifies which places (bits) of the IP address represent the network ID and therefore which bits automatically make up the range of the host ID. If you want to understand this in detail, it makes sense to look at a subnet mask in its binary form:
255.255.255.0 ≙ 11111111 11111111 11111111 00000000
In CIDR notation, this (class C) subnet mask would be /24, since the first 24 bits determine the network component of the IP address. It's possible to not only to fill octets completely with ones or zeros, but also to create more flexible subnets using VLSM. For example, the mask /25 corresponds to the binary value 11111111 11111111 11111111 10000000, which in turn (in dot-decimal notation) corresponds to 255.255.255.128.
Even with CIDR and VLSM, bits in subnet masks must always be filled from left to right and must not be randomly set to 1 or 0.
CIDR blocks: explanation and table
An IPv4 address consists of 32 bits. This becomes clear when you convert the decimal notation into the binary equivalent: 201.105.7.34 corresponds to 11001001 01101001 00000111 00100010. The binary notation – and the calculation method with which computers operate – of an IP address consists of 32 digits, which can either be 1 or 0: hence 32 bits. So, the possible suffixes in CIDR notation range from 0 to 32.
Creating subnets is about creating commonalities. 201.105.7.34/24 is in the same network as 201.105.7.1/24. The suffix signals that only the first 24 bits of the network component are counted. To do this, they have to be the same, if both addresses are to belong to the same network. The remaining bits are reserved for the host part. The number of bits that you see right after the slash in CIDR format indicates the number of digits (from left to right) that belong to the power supply of the IP address. The following table shows which subnet masks are behind the CIDR notation and how many host addresses they allow.
However, not all networks can also provide hosts. Networks with /31 have only 2 possible IP addresses for hosts, which would then have to be used for the network address (only 0s in the host part) and the broadcast address (only 1s in the host part). Two addresses are always reserved in each network: the network address (only 0s in the host part), which serves to identify the network, and the broadcast address (only 1s in the host part), which is used for transmission to all network participants. So, not all networks have the possibility to provide hosts. A /31 network has only 2 possible IP addresses, which must then be used for broadcast and network addresses. When looking at the CIDR table, then, two addresses must always be subtracted from the total available addresses. In the /32 network, however, only one address is available, and does not allow either broadcast nor network addresses.
The /0 network includes the complete address space. This contains only a large network with all possible IP addresses (minus two) as hosts so this doesn't really count as a subnet. The nets /1 to /7 are also not used for individual subnets. Since the possible number of hosts is too large, these networks are divided into further subnets.
Calculating CIDR: examples
The principle behind CIDR can be explained more clearly using examples. In the following, we will explain how it works in both subnetting as well as supernetting.
Subnetting
If you want to create subnets (especially flexible subnets), it is not enough to simply attach the same suffix to the IP address. It is important to understand what happens with binary conversion. 192.168.200.5/30 and 192.168.200.9/30 do not belong to the same network, for example. The reason for this can be seen when both addresses and the corresponding subnet mask are represented as binary numbers. A logical connective is then required. To do this, the two values are compared, which will only be transferred to the network address if there is a 1 at the same position. The combinations 0 ∧ 0 and 0 ∧ 1 result in zero.
Both addresses are therefore not in the same network. They would have been, however, if the second address had been 192.168.200.6/30.
To calculate which IP addresses are available to you in a subnet, you have to calculate the area. For example, a company has to accommodate 2.000 hosts in a network. The CIDR table tells us that we need a /21 network. Alternatively, this can also be calculated. To do this, you must create a logarithm: x=log2(2000). The result (≈10,666) is not a natural number, so you can round it up: 11. You can form a subnet with 211 hosts: 2,048 (two addresses for broadcast and network address need to be subtracted).
If you look at the table, you will see that the powers of 2 rise from (/32) to (/0). So, you could calculate 32-11 = 21 to get the required subnet suffix (/21).
The number assigned by this internet provider is (in our example) 210.105.44.170. We also transfer this information into binary notation and use the mask that has just been determined.
The first address – the network address that shouldn't be used – is 210.105.40.0/21. You have 2,046 IP addresses available between this and the broadcast address. The highest IP address (broadcast) is 210.105.47.255/21. Why is that? 2,048 (the maximum number of addresses in the subnet) divided by 256 (the number of possibilities in one octet) results in 8. This means that in the third octet the eight values from 40 to 47, and in the fourth octet, all values from 0 to 255, must be covered.
You can also save yourself the arithmetic work: there are some good online computers that will give you the area for your host addresses. In most cases, however, you still have to determine the required subnet size yourself. But you can find it in the corresponding table.
Supernetting
Let's assume that a company has three sites and three networks and their corresponding routers. It would make sense – also in the sense of the routing table – to turn it into a supernet. The three networks have the addresses 192.168.43.0, 192.168.44.0, and 192.168.45.0 (possible subnet masks next to the IP addresses of the networks are first relevant in this context). We first compare them in binary notation and only use the digits that all three addresses have in common – from left to right: From the first difference, all other digits are set to zero.
The network address of the supernet is therefore 192.168.40.0. To determine the corresponding subnet mask that belongs to this network, you count the places (bits) that led to the new IP address. In our example, these are 21 bits: 192.168.40.0/21.
Related articles